IMCTF : CTF by Ir0n Maiden Team at University of Nagoya
I checked some questions for a short time..
Welcome
https://twitter.com/nu_cybersec/status/1472038918522490880?s=20
png trick
Web
1. can you see cookie?
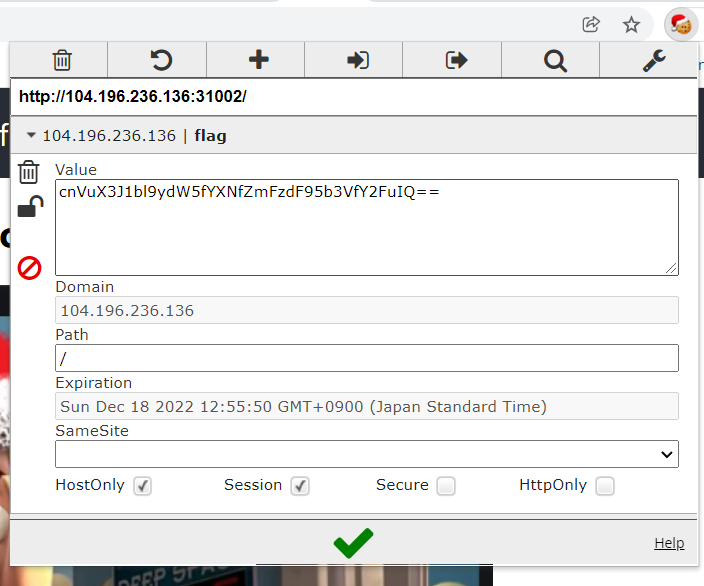
I already has a tool ( not using and almost forgot ) to see the cookie
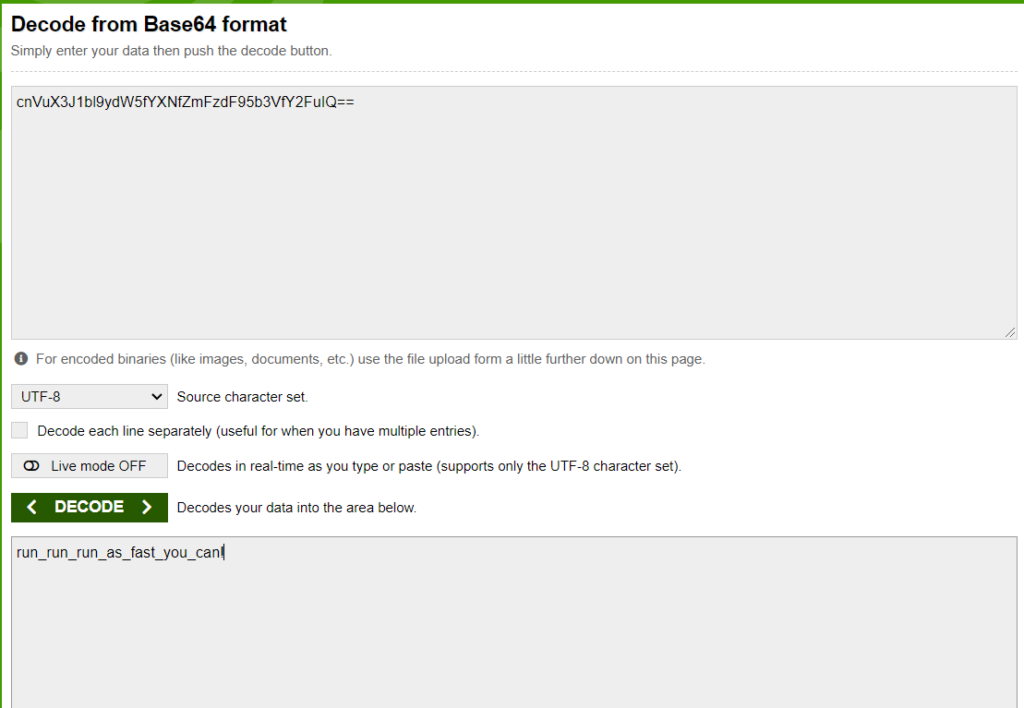
Base64
2. for stranger of storage
storage? It may be saying local or session storage
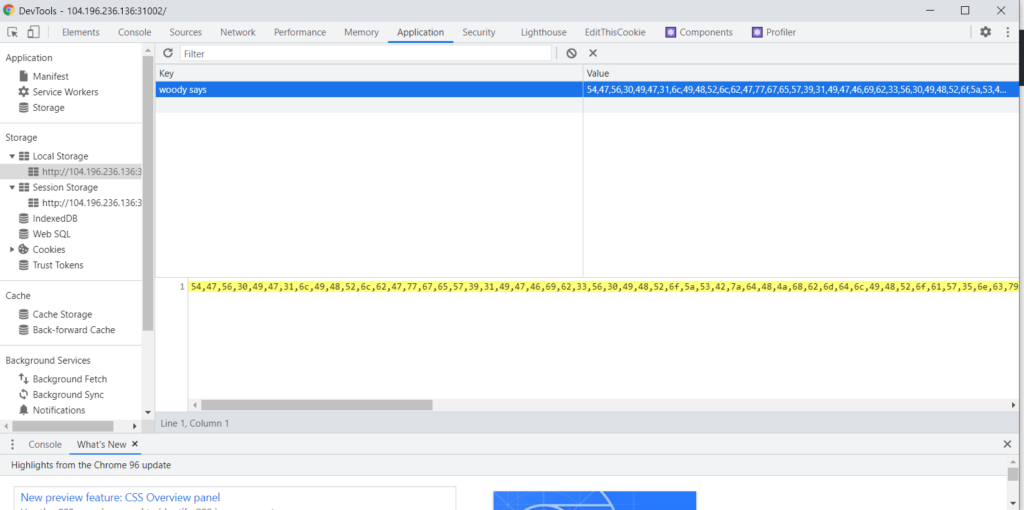
Find hex to ascii converter web… ( Dealing with these things mainly using web )
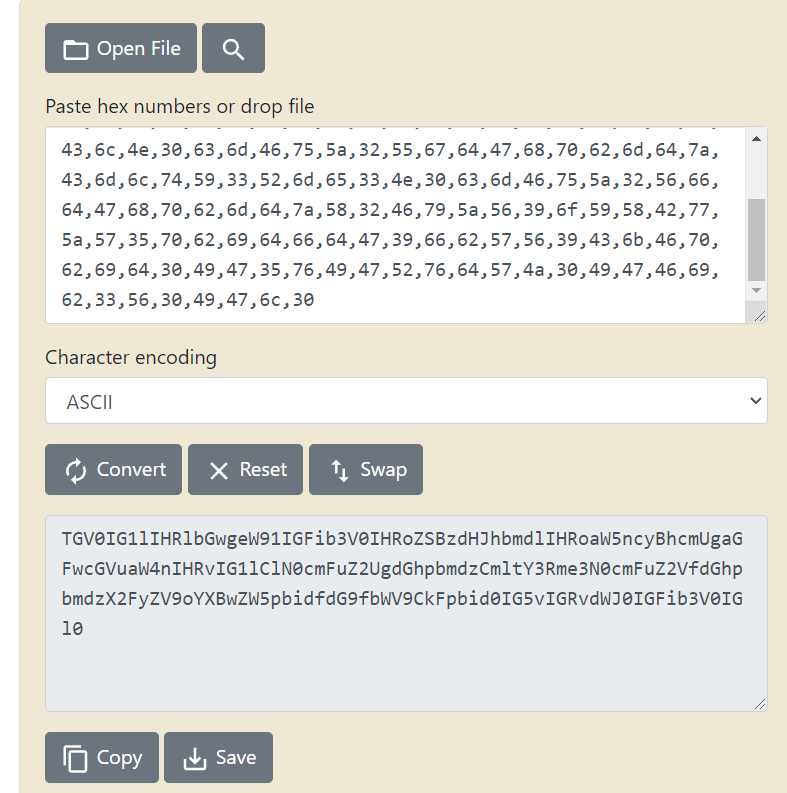
Base64 again
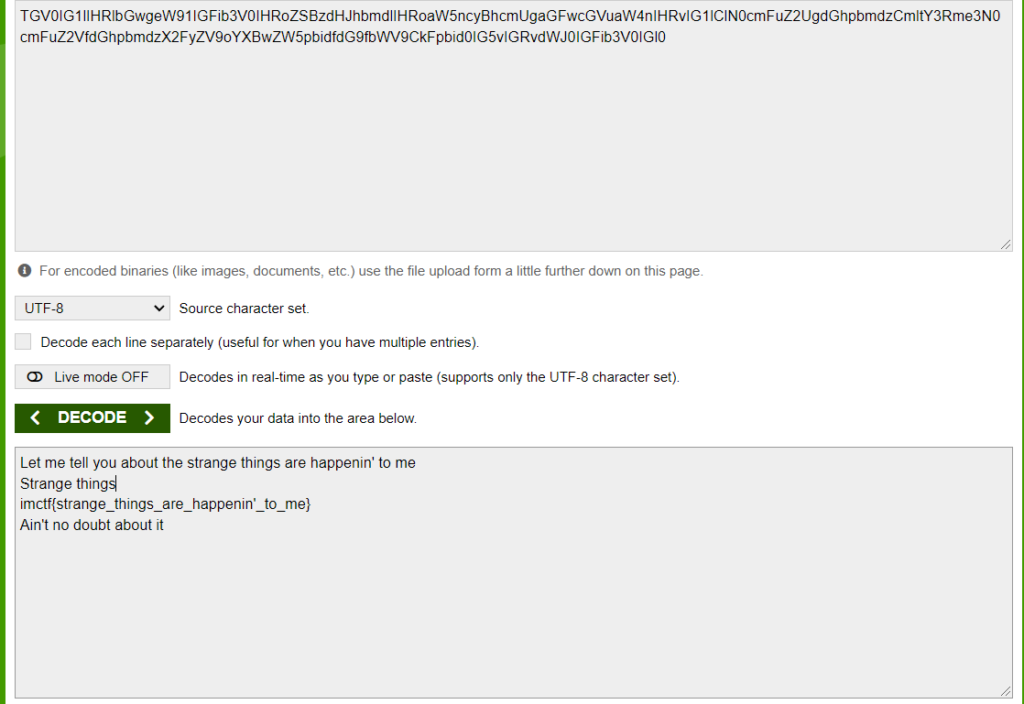
3. not any more logging
obfuscated javascript. ( Decoder)
'use strict';
var _0x50b41b = _0x2590;
(function (groupingFunction, val) {
var toMonths = _0x2590;
var data = groupingFunction();
for (; !![];) {
try {
var nodeval = parseInt(toMonths(317)) / (-8564 + 2421 + -6144 * -1) + parseInt(toMonths(287)) / (-2 * 1671 + -2819 + 6163 * 1) * (-parseInt(toMonths(289)) / (11 * 203 + -1057 * -7 + -9629)) + parseInt(toMonths(309)) / (-9074 + 29 * 171 + 4119) * (parseInt(toMonths(288)) / (-7 * -56 + 7191 + 3 * -2526)) + -parseInt(toMonths(308)) / (-7649 * -1 + 6529 * -1 + -1114) * (parseInt(toMonths(320)) / (1 * 8490 + -586 * -3 + -10241)) + -parseInt(toMonths(296)) / (-1076 + 7998 + 1 * -6914) * (parseInt(toMonths(313)) /
(445 * -11 + 581 + 393 * 11)) + -parseInt(toMonths(318)) / (-2 * 2930 + 9402 + -3532) + parseInt(toMonths(311)) / (2 * -2058 + -286 + 4413);
if (nodeval === val) {
break;
} else {
data["push"](data["shift"]());
}
} catch (_0x30eca5) {
data["push"](data["shift"]());
}
}
})(_0x57ae, 224071 * 7 + 1877649 + -2473965);
var _0x2967b8 = function () {
var y$$ = !![];
return function (ch, myPreferences) {
var voronoi = y$$ ? function () {
var getPreferenceKey = _0x2590;
if (myPreferences) {
var bytes = myPreferences[getPreferenceKey(310)](ch, arguments);
return myPreferences = null, bytes;
}
} : function () {};
return y$$ = ![], voronoi;
};
}();
var _0x962b9e = _0x2967b8(undefined, function () {
var parseInt = _0x2590;
var data = {};
data[parseInt(324)] = function (buckets, name) {
return buckets + name;
};
data[parseInt(295)] = parseInt(328) + "nction() ";
data[parseInt(330)] = parseInt(319) + parseInt(298) + 'rn this")(' + " )";
data[parseInt(326)] = function (rowTop, clientHeight) {
return rowTop < clientHeight;
};
data[parseInt(306)] = parseInt(290);
data[parseInt(300)] = parseInt(297);
var rows = data;
var callbackVals = parseInt(322)[parseInt(301)]("|");
var callbackCount = 211 * 35 + 8203 + -1299 * 12;
for (; !![];) {
switch (callbackVals[callbackCount++]) {
case "0":
var db = result["console"] = result[parseInt(314)] || {};
continue;
case "1":
try {
var evaluate = Function(rows[parseInt(324)](rows[parseInt(295)] + rows[parseInt(330)], ");"));
result = evaluate();
} catch (_0x19f1d0) {
result = window;
}
continue;
case "2":
var j = 1 * 6559 + -2 * 4079 + 1599;
for (; rows[parseInt(326)](j, names[parseInt(331)]); j++) {
var data = _0x2967b8[parseInt(325) + "r"][parseInt(307)][parseInt(312)](_0x2967b8);
var name = names[j];
var values = db[name] || data;
data[parseInt(286)] = _0x2967b8[parseInt(312)](_0x2967b8);
data["toString"] = values["toString"][parseInt(312)](values);
db[name] = data;
}
continue;
case "3":
var result;
continue;
case "4":
var names = ["log", "warn", parseInt(292), parseInt(305), parseInt(304), rows["_0x268d36"], rows[parseInt(300)]];
continue;
}
break;
}
});
function _0x2590(totalExpectedResults, entrySelector) {
var tiledImageBRs = _0x57ae();
return _0x2590 = function searchSelect2(totalExpectedResults, entrySelector) {
totalExpectedResults = totalExpectedResults - (-319 * -6 + -178 + -1450);
var tiledImageBR = tiledImageBRs[totalExpectedResults];
return tiledImageBR;
}, _0x2590(totalExpectedResults, entrySelector);
}
_0x962b9e();
function _0x55829c() {
var stringify = _0x2590;
var primaryReplicas = {
"_0x450522": function _cancelTransitioning(cb, TextureClass) {
return cb(TextureClass);
},
"_0x506b49": stringify(315) + stringify(291),
"_0x349f37": "imctf{is_t" + stringify(323) + stringify(316) + stringify(302)
};
primaryReplicas[stringify(294)](alert, primaryReplicas["_0x506b49"]);
console[stringify(303)](stringify(329) + "on't_need_" + "logging_an" + "y_more}");
console["clear"]();
console[stringify(303)](primaryReplicas["_0x349f37"]);
}
document[_0x50b41b(321) + _0x50b41b(327)]("root")["addEventLi" + _0x50b41b(293)](_0x50b41b(299), _0x55829c), console[_0x50b41b(303)] = function () {};
function _0x57ae() {
var expected = ["length", "__proto__", "461660lOjagx", "97690rUVzsh", "6dWjFYJ", "table", " imctf", "info", "stener", "_0x450522", "_0x3213de", "24ZXVGsU", "trace", 'ctor("retu', "click", "_0x2135f0", "split", "er?}", "log", "exception", "error", "_0x268d36", "prototype", "8940714kEIfNB", "24eYMmjc", "apply", "41941867XQHRnr", "bind", "4980888MkjIqS", "console", "welcome to", "final_answ", "1158226zTrKzX", "5040950RgDVYO", "{}.constru", "7hjjMwm", "getElement", "3|1|0|4|2", "his_flag?_", "_0x3e4895",
"constructo", "_0x49e28b", "ById", "return (fu", "imctf{we_d", "_0x3e841e"
];
_0x57ae = function browserCheck() {
return expected;
};
return _0x57ae();
};
maybe we can remove clear from here but.. logging something like flag at console before clearing console and I see `imctf{we_d` inside expected lol ^^
Maybe something looks like flag above may be fake since I see some fakes in expected.
imctf{we_don’t_need_logging_any_more)
Osint
1. Ready made default
君は産業スパイとしての身分を隠し、ライバル会社のキーパーソンとの友人関係を構築。自宅へ招かれ、クリスマスの夕食を共にすることになった。相手が席を外したので、Wi-Fi ルーターのパスワードを調べることにした。SSID は TP-Link_3F04_5G だ。まったく、豪邸は敷地の外まで Wi-Fi が届かなくて厄介だな。
フラグ形式 : imctf{ + usename + _ + password + }
TP-Link default id/pw is admin / admin so imctf{admin_admin} is the flag